Getting Started📜
What is a service mesh?📜
In modern software development, developers create applications by distributing them into collections of microservices. Each collection of microservices is responsible for handling specific business functions. A service mesh is a dedicated infrastructure layer that can enhance the capabilities of your application. It enables you to integrate observability, traffic management, and security without modifying your code. Service mesh refers to the software used to implement this pattern and the network domain or security framework it establishes.
As you deploy distributed services, like in a Kubernetes-based system, managing and understanding them becomes more challenging due to their expanding size and complexity. Its requirements include discovery, load balancing, failure recovery, metrics, and monitoring. A service mesh also often addresses more complex operational needs, like A/B testing, canary deployments, rate limiting, access control, encryption, and end-to-end authentication.
A distributed application relies on service-to-service communication for its operation. As you add additional services, it becomes more complicated to route communication within and between application clusters. Istio makes things less complex and reduces the workload for development teams.
Additional resources:
- Definition of a service mesh
- When and why to utilize a service mesh with microservices
- What is Istio?
What is Istio?📜
Istio is an open-source service mesh that layers transparently onto existing distributed applications. Istio’s features provide an organized and efficient way to secure, connect, and monitor services. Istio is the path to load balancing, service-to-service authentication, and monitoring – with few or no service code changes. Its powerful control plane brings vital features, including:
- Secure service-to-service communication in a cluster with TLS encryption, strong identity-based authentication and authorization.
- Automatic load balancing for HTTP, gRPC, WebSocket, and TCP traffic.
- Fine-grained control of traffic behavior with rich routing rules, retries, failovers, and fault injection.
- A pluggable policy layer and configuration API supporting access controls, rate limits and quotas.
- Automatic metrics, logs, and traces for all traffic within a cluster, including cluster ingress and egress.
Istio is built to be flexible and can handle various deployment requirements. Istio’s control plane operates on Kubernetes, allowing you to include applications deployed in that cluster into your mesh. Additionally, you can expand the mesh to include other clusters or connect with VMs and endpoints outside of Kubernetes.
Many contributors, partners, integrations, and distributors actively extend and utilize Istio in various scenarios. You can install Istio yourself, or several vendors have products that integrate Istio and manage it for you.
How Istio works📜
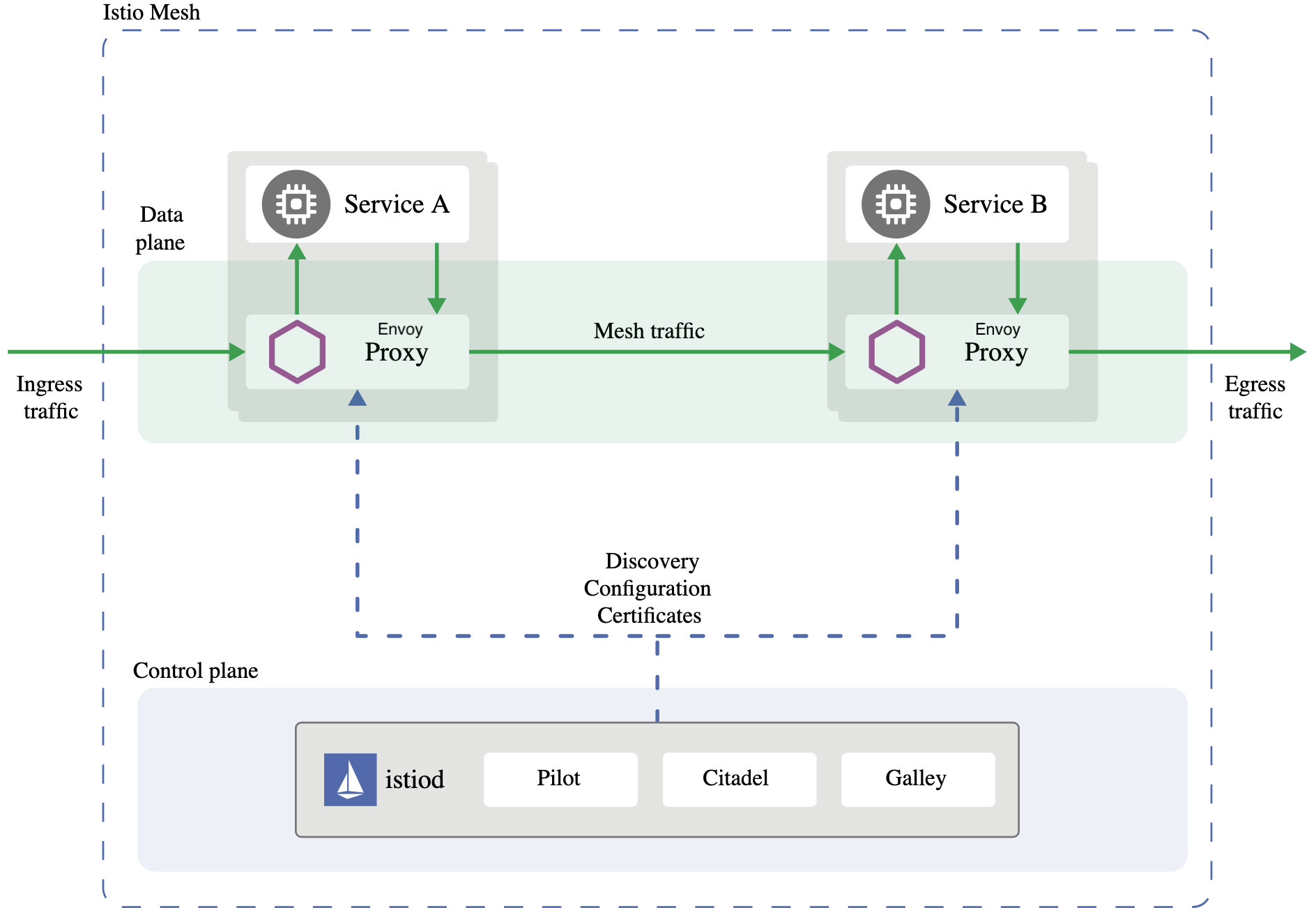
Istio has two main components: - the data plane, and - the control plane.
The data plane is the communication between services. A service mesh must be present for the network to understand the traffic sent over and decide based on its type, source, or destination.
A service mesh utilizes a proxy to intercept all your network traffic, enabling a wide range of application-aware features based on the configuration you define.
An Envoy proxy deploys with each service you start in your cluster or runs alongside services running on VMs.
The control plane uses your preferred settings and service preferences to program proxy servers, which update automatically when changes occur to the rules or environment.
Concepts📜
Traffic management📜
Routing traffic, both within a single cluster and across clusters, affects performance and enables better deployment strategy. Istio’s traffic routing rules let you easily control the flow of traffic and API calls between services. Istio simplifies the configuration of service-level properties like circuit breakers, timeouts, and retries. It makes setting up essential tasks like A/B testing, canary deployments, and staged rollouts with percentage-based traffic splits easy.
Observability📜
As services grow in complexity, it becomes challenging to understand behavior and performance. Istio generates detailed telemetry for all communications within a service mesh. This telemetry allows operators to observe how their service behaves, which helps them troubleshoot, maintain, and optimize their applications. Operators can use most of these instruments without requiring application changes. Through Istio, operators gain a thorough understanding of how monitored services interact.
Istio’s telemetry includes detailed metrics, distributed traces, and full-access logs. With Istio, you get complete and comprehensive service mesh observability.
Security📜
Microservices have particular security needs, including protection against man-in-the-middle attacks, flexible access controls, auditing tools, and mutual TLS. Istio includes a comprehensive security solution allowing operators to address these issues. It provides a strong identity, assertive policy, transparent TLS encryption, authentication, authorization, and audit (AAA) tools to protect your services and data.
Istio’s security model is based on security by default, aiming to provide an in-depth defense to allow you to deploy security-minded applications even across distrusted networks.
For more information on Istio, refer to Istio docs for documentation.
Using Istio in Big Bang📜
See our guide to standup a minimal cluster with Istio on your VM Big Bang Quickstart.
What is next?📜
Now that we can access our environment and Kubernetes cluster, we can validate Istio’s installation.